
Linux Administration and DevOps Training: Why To Go For in the New Age IT Landscape?
Wed, 13 Sep 2023
0
.png)

Unveiling the Future: Top 10 Emerging Tech Skills for Your Dream Job in 2024
Mon, 18 Dec 2023
0
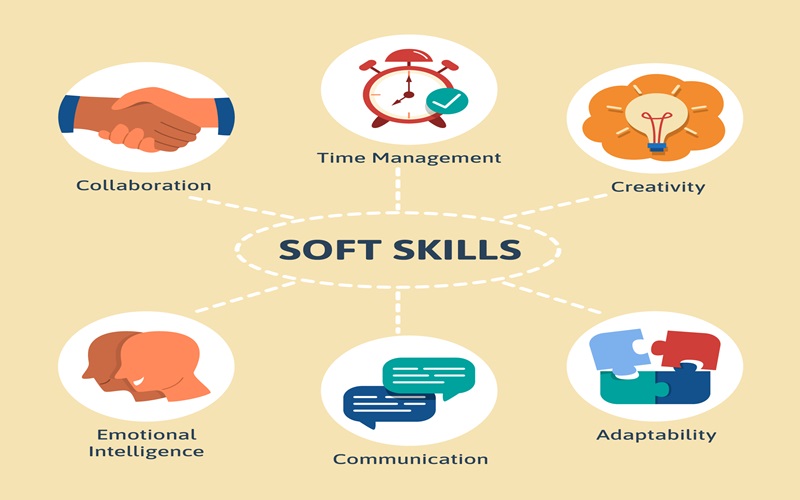
The Power of Soft Skills: How Communication and Teamwork Can Boost Your Tech Career
Mon, 18 Dec 2023
0

Mastering Time Management: Hacks for Staying Productive in a Tech-Driven World
Tue, 19 Dec 2023
0

Data Privacy in the Age of Big Tech: How to protect your online information
Tue, 19 Dec 2023
0
 (1).png)

Search
Popular categories
Information Technology
108Career
46Entertainment
12Education
3Latest blogs
 (29).png)
Zero Trust Security and the SOC: Why SOCs Are Essential in a Zero Trust World
5 Days Ago
 (28).png)
Phishing Scams: How to Spot, Avoid, and Defend Against Them
5 Days Ago
 (28).png)
Phishing Scams: How to Spot, Avoid, and Defend Against Them ????????
5 Days Ago

 PaniTech Academy
PaniTech Academy  Content Writer
Content Writer  PaniTech Academy
PaniTech Academy
Write a public review